Cloud Management
Broad awareness of the benefits and cost savings that commercial cloud computing offers has prompted policy mandates across Federal agencies to drive adoption and phase out continued investments in traditional on-premise “legacy” data centers.
Raven Solutions provides full-service solutions to migrate existing IT systems into government-approved, commercial cloud environments and rapidly accelerate cloud adoption while complying with DISA's Secure Cloud Computing Architecture (SCCA) requirements. Leverage our framework of tools, processes and methodologies for securing, re-hosting, refactoring or re-developing legacy applications.

Account Provisioning
Cloud service provider (CSP) accounts provide a natural boundary for workload environments (Production, Staging, Testing, Development) and limit the impact of a critical event, such as a security breach, by reducing blast-radius.
Accounts form the foundation of mission owner enclaves and are used to segment workloads or shared services. Raven Solutions provides automated provisioning of CSP accounts based on the Center for Internet Security (CIS) Foundations Benchmark, a set of security configuration best practices.
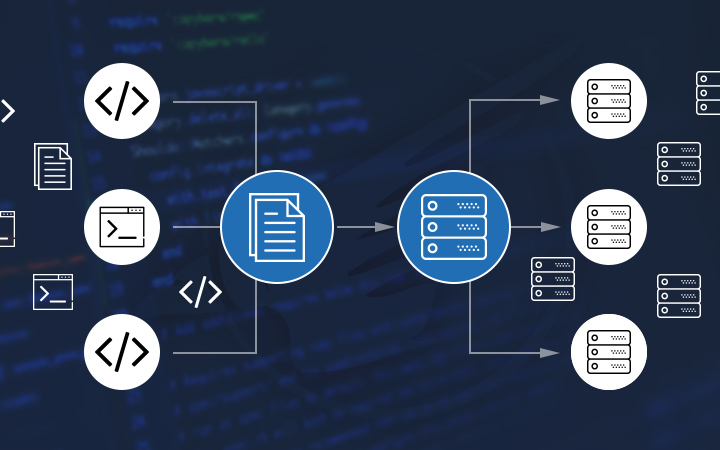
Infrastructure as Code (IoC)
Cloud computing takes advantage of virtualization to enable on-demand provisioning of compute, network and storage resources that constitute network infrastructures. Software-defined infrastructure facilitates the creation of “code” that defines an entire network infrastructure.
Raven Solutions maintains a catalog of network infrastructure templates that provide consistent, reusable architecture resources with security configurations that map to NIST 800-53 control requirements. As a result, our customers have the advantage of being able to leverage a common software infrastructure library the generate audit ready cloud resources.
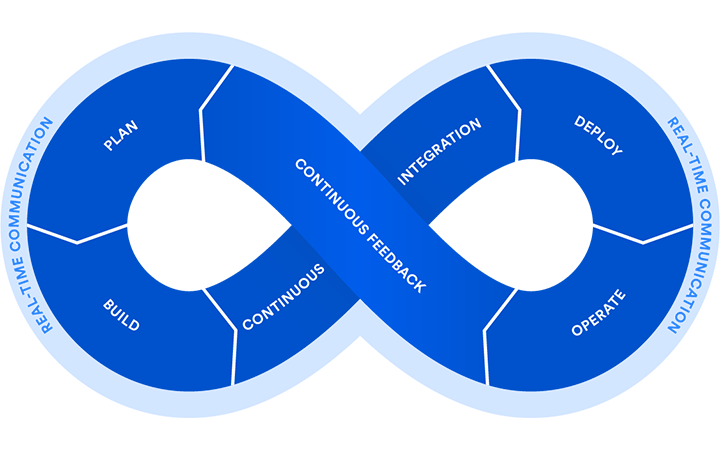
DevSecOps
Our experience in managing highly secure environments has proven that by closely integrating development and operations (DevOps) with security and operations (SecOps), a high operational tempo can be sustained without compromising network security.
Instead of delivering big, infrequent releases (once every few months) like traditional development teams, DevOps teams take a “continuous delivery” approach. This means releasing small, incremental improvements regularly—often several times per day. DevSecOps profoundly impacts all operations and maintenance activities and is often regarded as the key indicator of cloud maturity.
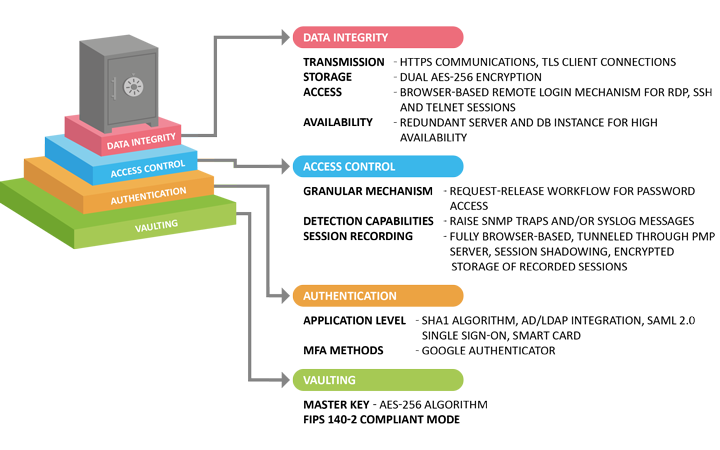
Trusted Cloud Credential Manager (TCCM)
Enforce policy based access for privileged accounts. Credentials are stored in a FIPS 140-2 secure vault and administrative access is tightly monitored via fine grain policies that require request authorization to a limited time based access grant without exposing credentials.

Shared Security Service
Isolate mission owner workloads from shared security services that provide Virtual Datacenter Security Stack (network security) and Virtual Datacenter Managed Services (host based security). Establishing a security trust relationship between CSP accounts allows new workloads to inherit a large portion of the security control implementation and centralizes security monitoring, logging and management.
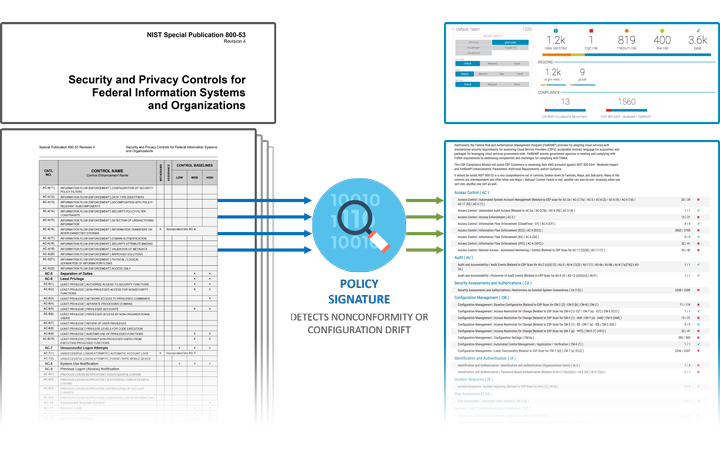
Risk Management Framework Compliance
Standardized architecture templates enforce organizational policies and security requirements. Continuous monitoring tools and dashboards provide near real time updates on compliance status for NIST 800-53 controls. If a configuration drift occurs, automation events alert cybersecurity personnel. Certain events may trigger automated remediation actions to restore the approved configuration and record the event for forensic analysis.

Managed Services
Raven Solutions provides a suite managed services specifically designed for Federal agencies to centralize governance of architecture, operations, security, continuous monitoring and authentication across cloud service provider accounts.
Our professional services provide turn-key operational support including:
- Hardened virtual machine images (STIG Complaint)
- 1Cost optimization and metering
- Consolidated billing
- Incident response
- Disaster recovery
- Patch management (IAVA/B)
- Security as service (continuous monitoring)
- Cybersecurity documentation (Policy, SOP, guidelines/procedures, RMF body of evidence)
Mission owner support services (MOSS)
Raven Solutions provides a suite of support solutions to provide enhanced productivity for mission owners:
-
Single Sign On
Single Sign-On provides centralized access to mission owner back office applications. Reduce risk by standardizing management, operational and technical security controls for authentication and authorization. -
Issue/task management
Centralize governance of support and application change requests. Standardize triage and change control processes and gain full visibility of development and release cycles. -
Application Performance Management
Monitor key performance metrics of applications and identify application performance issues. Resolve performance degradation issues no matter where they originate. Gain visibility into the minutest details from browser experience right down to an individual line of code or slow database queries.